# WEEK3
# 阳光开朗大男孩
得到两个 txt 文件
flag.txt:
1 | 🙃💵🌿🎤🚪🌏🐎🥋🚫😆😍🌊⏩🔬🚹✉☀☺🚹🐅🎤🛩💵🌿🌊🚰😊🌊✉🐎❓🎈🌉👑🎅📮🥋👣🕹🚪☀🔄🚫🐍❓🐍😊☀🔬🍍🤣🎈🥋🙃👑🌏🐎🌊📮😂💵🏹👉❓😇🍴💧☺💵😁☃👉🎅👁☂🌿👉🍴🌪👌🍴🍵🖐😇🍍😀🗒🗒 |
secret.txt:
1 | 法治自由公正爱国公正敬业法治和谐平等友善敬业法治富强公正民主法治和谐法治和谐法治法治公正友善敬业法治文明公正自由平等诚信平等公正敬业法治和谐平等友善敬业法治和谐和谐富强和谐富强和谐富强平等友善敬业公正爱国和谐自由法治文明公正自由平等友善敬业法治富强和谐自由法治和谐法治和谐法治和谐法治法治和谐富强法治文明公正自由公正自由公正自由公正自由 |
猜测是 emoji-aes 加密,secret 便是 key
secret 社会主义核心价值观编码解码得到:this_password_is_s000_h4rd_p4sssw0rdddd
is 后面的作为 key:s000_h4rd_p4sssw0rdddd
emoji-aes 解密:
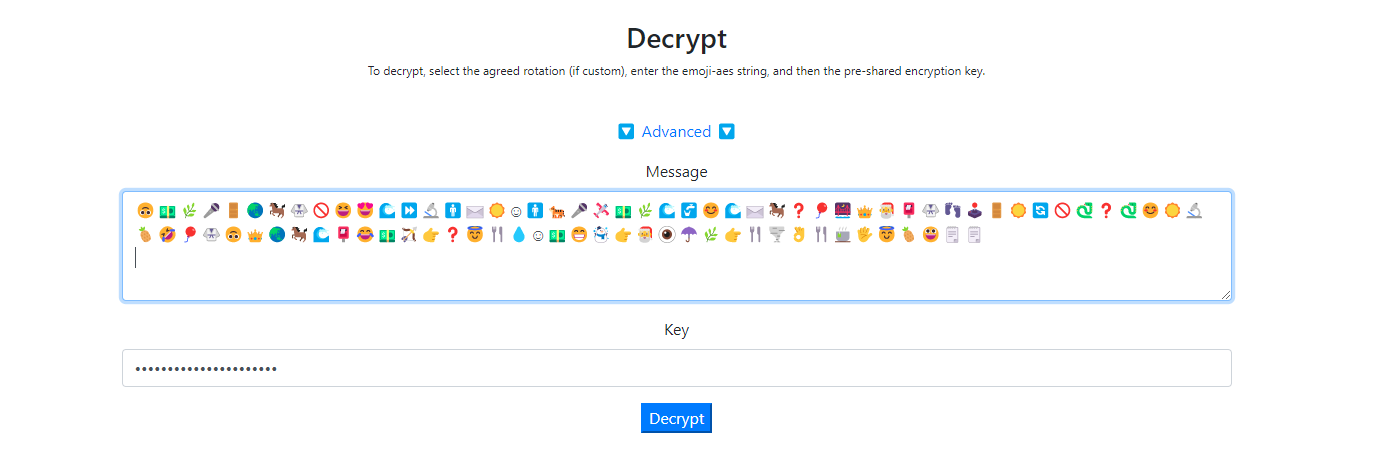
得到 flag
flag{3m0ji_1s_s0000_1nt3rest1ng_0861aada1050}
# 大怨种
拿到 gif 文件,使用 gifsplitter 进行分离
得到二维码

使用网站进行扫描
https://products.aspose.app/barcode/recognize#
得到字符串:
1 | 666C61677B315F64306E745F6B306E775F6830775F746F5F7363346E5F746831735F633064335F61cef808a868e} |
后半段为明文字符串:cef808a868e}
前半段进行 16 进制转换后为 flag
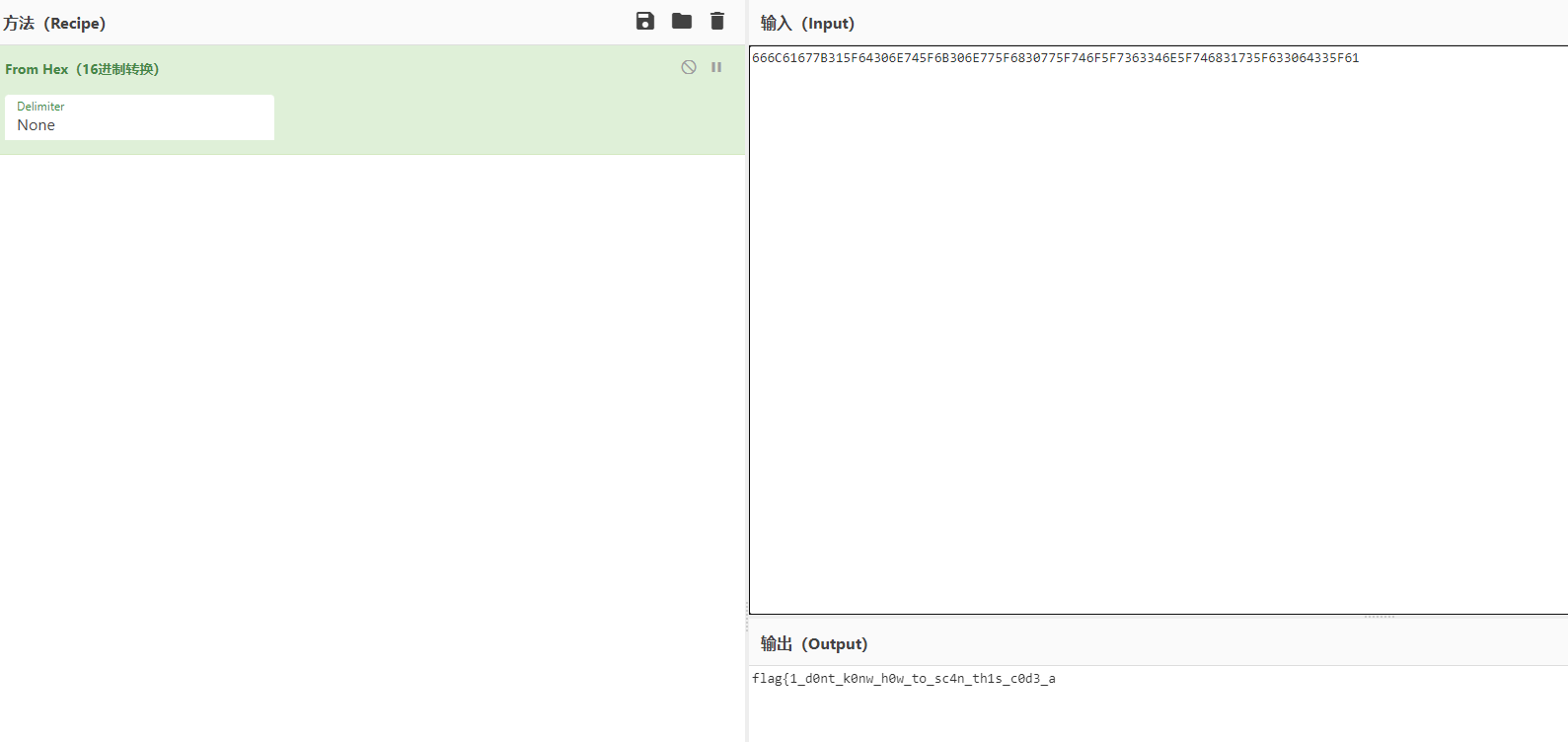
flag{1_d0nt_k0nw_h0w_to_sc4n_th1s_c0d3_acef808a868e}
# 2 - 分析
拿到流量包

在流 30 找到了攻击者登录使用的用户名
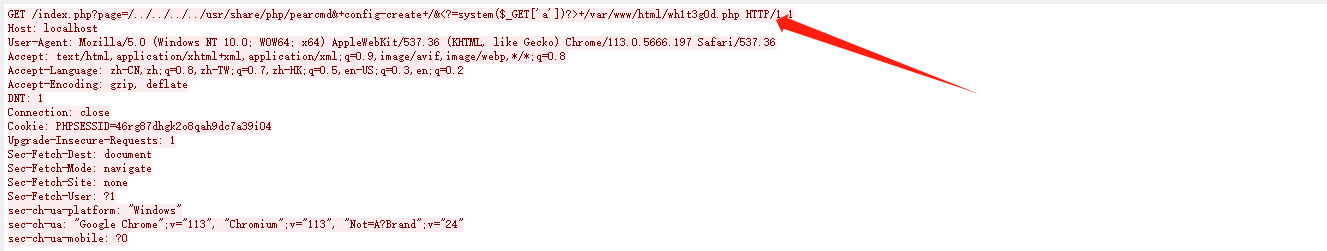
在流 33 看到了利用 index.php 进行了一个写马的的操作,也就是说存在漏洞的文件名为 index.php,而被写入一句话木马的文件 wh1t3g0d.php 便是 webshell 文件名
1 | flag{best_admin_index.php_wh1t3g0d.php} |
将括号内 md5 之后便是 flag
flag{**4069afd7089f7363198d899385ad688b}**
# 键盘侠
同样是一个流量包
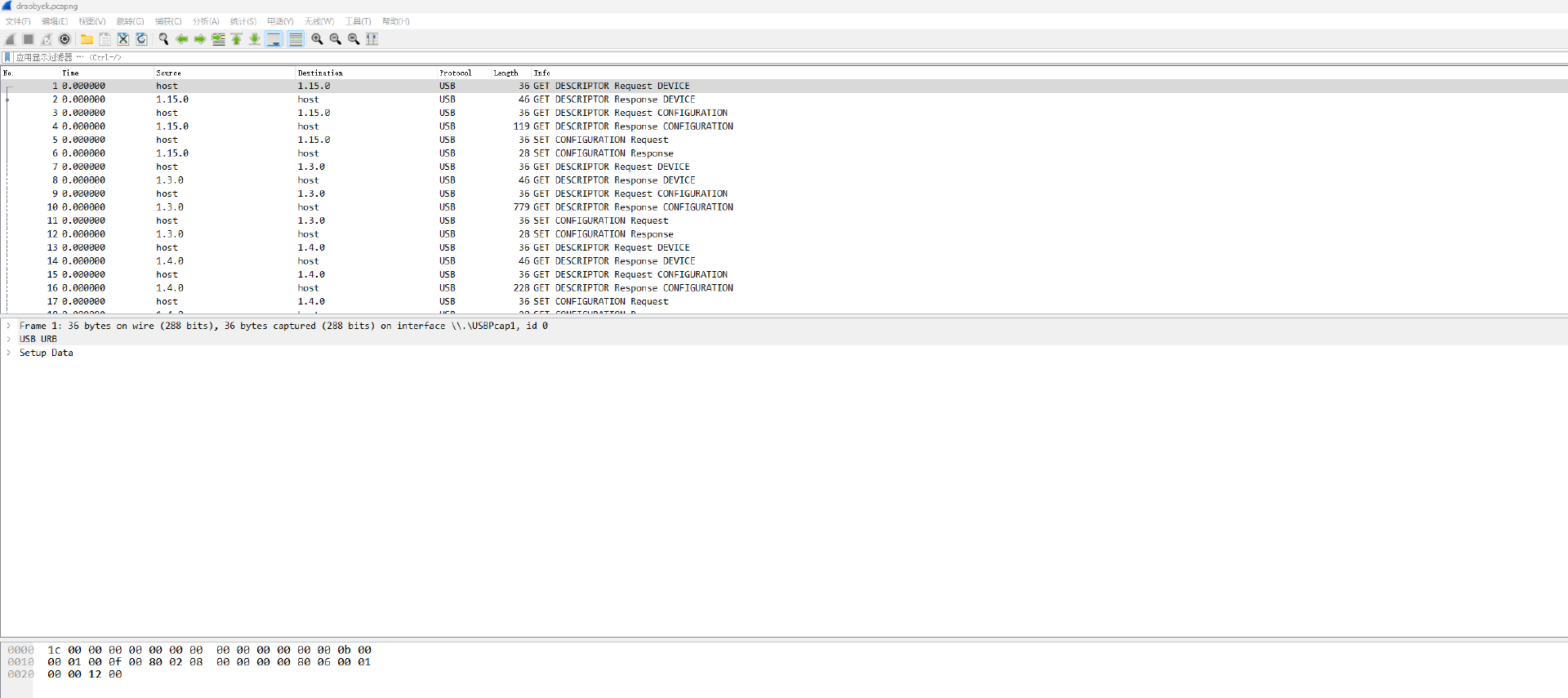
发现是 usb 的流量,又是老知识点了
先翻翻流量看看 data 数据
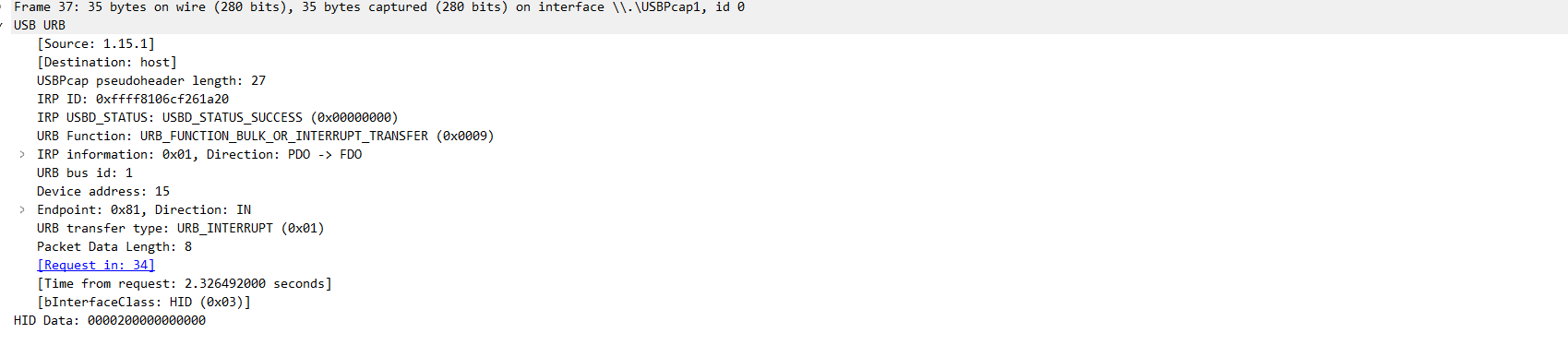
发现 HID data 是 8 字节的数据,猜测为键盘流量,先用 tshark 进行导出
1 | tshark -r draobyek.pcapng -T fields -e usbhid.data > usbdata.txt |
得到 usbdata.txt 之后再进行删除空行添加冒号的操作
1 | #!/usr/bin/env python |

得到 out.txt
再用脚本进行对照解密
1 | #!/usr/bin/env python |
输出:
1 | w3lc0m3<SPACE>to<SPACE>newstar<SPACE>ctf<SPACE>2023<SPACE>flag<SPACE>is<SPACE>here<SPACE>vbafjwrisgjadwwiihdgja13882hxbbbna <CAP><CAP>ff<DEL>lll<DEL><DEL>aaa<DEL><DEL>gggg<DEL><DEL><DEL>{999<DEL><DEL>999<DEL><DEL>11<DEL>9aaa<DEL><DEL><SPACE><SPACE><DEL><DEL>eb2---<DEL><DEL>a450---<DEL><DEL>2f5f<SPACE><SPACE><SPACE><DEL><DEL><DEL>--<DEL>7bfc[unknown][unknown][unknown]-8989<DEL><DEL>dfdf<DEL><DEL>4bfa4bfa<DEL><DEL><DEL><DEL>85848584}}}<DEL><DEL><DEL><DEL><DEL><DEL><DEL>}]<SPACE><SPACE><SPACE><SPACE>nice<SPACE>work!1you<SPACE>got<SPACE>this<SPACE>flag |
在上一行可以看到解出来的其实是小写字母,于是把 FLAG {9919AEB2-A450-2F5F-7BFC-89DF4BFA8584} 换成小写就是最终 flag 了
flag {9919aeb2-a450-2f5f-7bfc-89df4bfa8584}
# 滴滴滴
拿到一张图片和一个音频,听了下应该是手机拨号的声音,还是老知识点了:DTMF 拨号音识别
利用 dtmf2num 命令进行识别
1 | dtmf2num 奇怪的音频.wav |
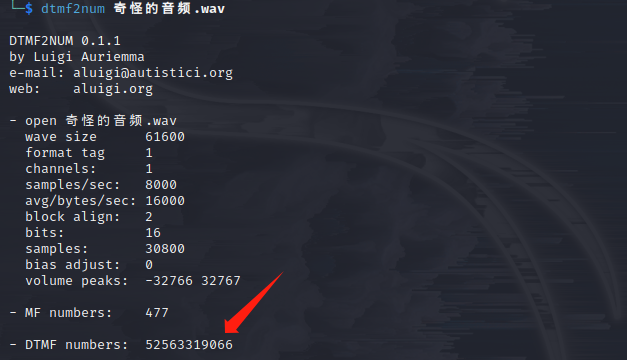
得到号码 52563319066,根据题目提示这应该是作为 jpg 的密码,猜测为 steghide 隐写
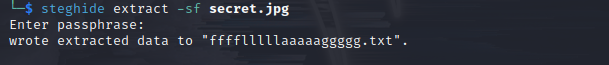
得到 flag
flag{1nf0rm4t10n_s3cur1ty_1s_a_g00d_j0b_94e0308b}
